Sign Up For Our Newsletter
Thank you for signing up!
Something went wrong! Please try again.
© 2026 AnChain.AI. All Rights Reserved | Privacy Policy

In August 2025, a San Francisco resident urgently contacted AnChain.AI after discovering over $1 million in cryptocurrency missing from his MetaMask wallet — primarily USDT (Tether) and USDC (Circle) stablecoins across Ethereum and Arbitrum blockchains.
The theft was the result of a highly sophisticated job recruitment scam. Unlike typical phishing attempts, this attack combined:
This case also highlights the regulatory urgency behind the GENIUS Act (2024), which established stricter oversight of digital assets in the U.S. and raised the bar for incident reporting, AML compliance, and fraud prevention. Under this new framework, organizations cannot treat crypto breaches as isolated incidents — they are now compliance and regulatory events with material consequences.
In this article, we detail the attack vector, the incident response workflow, and critical precautions professionals should take when engaging with recruiters on LinkedIn and other job platforms.
This investigation was made possible through close collaboration with our partners, including:
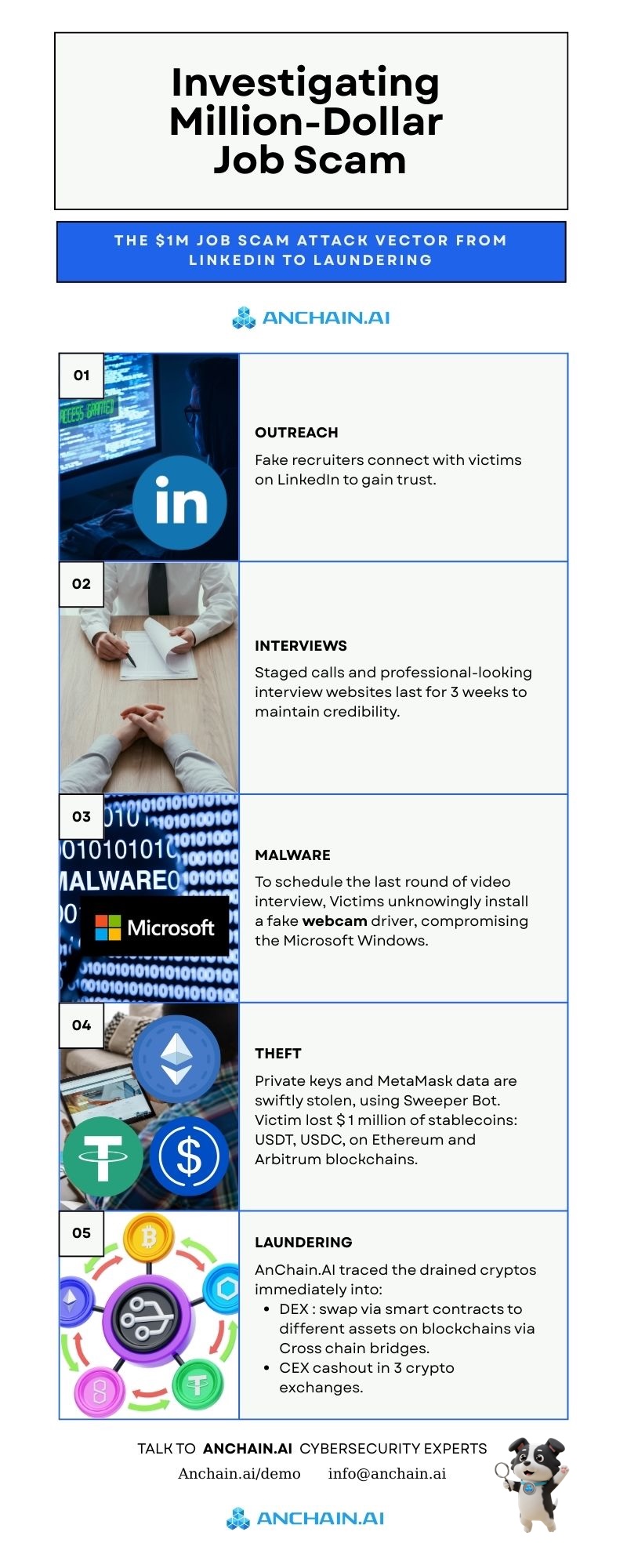
Social engineering continues to be the most effective initial access vector in cybercrime. According to Verizon’s 2024 DBIR, 74% of breaches involve a human element, [link] including phishing and pretexting. In the cryptocurrency ecosystem, this risk is amplified: attackers not only compromise endpoints but also directly drain digital wallets, resulting in irreversible financial loss.
In a recent case investigated by AnChain.AI, attackers combined LinkedIn recruitment scams, malware delivery, and cross-chain laundering to steal and obfuscate millions in digital assets.
The operation began with a fake recruiter profile, impersonating an HR manager at a well-known multinational. The profile featured:
This tactic is not isolated. LinkedIn reported in 2023 that tens of millions of fake accounts are blocked annually, yet sophisticated actors continue to exploit professional trust. Under the GENIUS Act framework, platforms like LinkedIn face growing pressure to strengthen KYC, AML, and anti-fraud defenses.

Over three weeks, the victim engaged in multiple interview rounds, including scheduled video calls. Attackers leveraged:
This extended vetting process lowered the victim’s guard, illustrating how AI is now weaponized to scale trust exploitation. Gartner predicts that by 2026, 30% of deepfake content online will be used for malicious purposes, up from less than 5% in 2022.
Before the final interview, the victim was asked to install a webcam driver and run command-line “compatibility tests.” In reality, this was a Windows malware dropper. Technical payload analysis showed it:
Such clipboard hijackers remain widespread: in 2024, Microsoft Threat Intelligence flagged over 7,000 malware families that target cryptocurrency wallet strings.
Within hours of compromise, attackers executed automated sweeps of hot wallets:
Once consolidated, attackers initiated a laundering cycle:
This tactic exploits weaker analytics coverage on L2 blockchain and cross-chain bridges, making them one of the most abused infrastructures in crypto crime.
👉 For a deeper dive: AnChain.AI blog on Cross-Chain Bridge Tracing
Despite these obfuscation attempts, AnChain.AI’s AutoTrace™ platform enabled investigators to:
Rapid tracing allowed exchange freezes and law enforcement alerts before the assets could be fully laundered through mixers or fiat off-ramps.

When crypto assets are stolen, every minute matters. AnChain.AI’s incident response combines digital forensics, blockchain tracing, and law enforcement coordination to contain damage and maximize recovery. The workflow below illustrates how our team neutralized a sophisticated job-scam–driven attack within hours.
1. Computer Forensics
2. Blockchain AutoTrace™
3. Law Enforcement & Exchange Coordination
4. Post-Breach Advisory

As the crypto ecosystem scales, regulators, platforms, and enterprises must treat social engineering + cross-chain laundering as one continuous kill chain, requiring integrated defenses from user education to blockchain analytics.
1️⃣ Verify recruiters on LinkedIn through official company emails or HR directories.
2️⃣ Never install drivers, apps, or tools sent by strangers.
3️⃣ Never store passphrases in plain text on your computer or cloud services.
4️⃣ Secure your wallets with hardware devices and multi-sig; don’t rely solely on browser wallets.
5️⃣ Act fast — contact a trusted cryptocurrency incident response provider immediately. Every minute counts.
This case underscores how job scams blend human deception with technical exploitation, leading to catastrophic financial losses.
At AnChain.AI, our blockchain forensics expertise, AI-powered AutoTrace™, and close coordination with law enforcement enable us to respond within hours, not weeks — often determining the difference between total loss and meaningful recovery.
👉 If your organization or friend faces crypto incidents, contact AnChain.AI today.
