Sign Up For Our Newsletter
Thank you for signing up!
Something went wrong! Please try again.
© 2026 AnChain.AI. All Rights Reserved | Privacy Policy
How Model Context Protocol (MCP) tools on AnChain.AI platform can transform a complex blockchain investigation from weeks of manual work into a comprehensive analysis completed in minutes
In late 2024, Chen Zhi (also known as Vincent Chen), the head of Prince Group, was arrested and charged with operating one of the largest pig butchering operations in history, a criminal enterprise estimated to have defrauded victims of over $15 billion. Read our Prince Group empire blog for details.
Pig butchering scams are sophisticated romance fraud schemes where criminals build trust with victims over weeks or months, then convince them to invest in fake cryptocurrency platforms. The victims' funds are stolen, and the criminals disappear. Chen Zhi's operation was particularly brazen, operating across multiple jurisdictions and using a complex network of shell companies and cryptocurrency addresses to launder the proceeds.
The Prince Group, based in Cambodia with operations spanning Hong Kong, the British Virgin Islands, and other jurisdictions, was designated as a Transnational Criminal Organization (TCO) by the US Treasury's Office of Foreign Assets Control (OFAC). Chen Zhi himself was added to sanctions lists by both the United States and United Kingdom.

But here's the critical question: How do you investigate and map a criminal cryptocurrency network when you only have a name and a company?
This is where blockchain intelligence and modern investigation tools become essential, and where AnChain.AI's MCP servers demonstrate their power.
Traditional financial investigations rely on bank records, wire transfers, and paper trails. Cryptocurrency investigations are fundamentally different. When you're dealing with blockchain transactions, you need to:
For the Chen Zhi investigation, we started with just a name and a company. The challenge was to find his cryptocurrency addresses, understand how they were being used, and map the entire criminal network.
AnChain.AI provides a suite of MCP servers that enable AI assistants and automated systems to perform comprehensive blockchain investigations. These tools integrate directly into investigation workflows, allowing analysts to query blockchain data, screen addresses, and trace transactions programmatically.
Let’s dive into how our sanctions screening agent was able to leverage AnChain Data MCP to build a complete picture of Chen Zhi's cryptocurrency operations:
The agent started by screening Chen Zhi's name against global sanctions databases. This immediately revealed:
OFAC Designation: Chen Zhi is listed as a Specially Designated National (SDN) under the Transnational Criminal Organization programUK HMT Designation: Also sanctioned under the UK's Human Rights programMultiple Identities: The screening revealed aliases (Vincent Chen), multiple passport numbers, and citizenship in three countries (Cambodia, Cyprus, Vanuatu)Associated Entities: The search also identified multiple Prince Group entities, all sanctionedKey Finding: The sanctions screening returned 10 Bitcoin addresses directly associated with Chen Zhi in the OFAC SDN listing. This is critical intelligence because these addresses are now legally blocked for all US persons and entities.
bc1q9kja7t2zxz0ze4lcgxf0l07pygpc69ws528lj9bc1qw75cxmxz4e2v265mue9wmqgq2m0qdyr25l2ufl386sPhHBbLidzPnoxUH74jiiYkHYtobefQbc1qw0pswznckx7s6tjmd2f5hrx4q6kc5nyrdxku50374RguZDMNW5Zh5ouW3KhKDcrerKusmsukbc1qnq3pzsw3elkecrw8pqrz70r7zuse6cwyxa6dhc bc1qeth6n6ryxexvkx34wnx3nuynun4474h3j0gkhw 35irs2AU6pVgenYbWvMRz22avDBLC9XMkdbc1qu4p4eynzu8vwwcv0yxq74gth00exjyech05uf0bc1q2we5eqjj8je6lz9xwjattpc3pn4jejc5h0s70f
Why This Matters: AnChain's sanctions screening doesn't just check names, it returns the actual cryptocurrency addresses associated with sanctioned entities. This is data that's often buried in PDFs or spreadsheets, but AnChain makes it immediately queryable and actionable.
This is where AnChain's unique intelligence capabilities really shine. The agent used the activity screening MCP to reveal detailed transaction patterns for each address:
Address #4: The Central Hub
One address stood out immediately: bc1qw0pswznckx7s6tjmd2f5hrx4q6kc5nyrdxku50
Activity Profile:
What This Tells Us:
Address #1: The Distribution Network
Another address, bc1q9kja7t2zxz0ze4lcgxf0l07pygpc69ws528lj9, showed a different pattern:
Pattern Recognition: The consistent source address and regular transfer amounts suggest an automated collection system, possibly a fake exchange or investment platform collecting funds from victims.
The attribution screening revealed the transaction flow patterns, showing how funds move through the network:
Key Network Structure Identified:
Inter-Address Connections:
What Makes This Unique: AnChain's sanctions screening doesn't just query a static database, it integrates with official OFAC and UK HMT sanctions lists and returns structured data including cryptocurrency addresses. When we searched for "Chen Zhi," we didn't just get a "yes, he's sanctioned" response, we got:
This integration saves investigators hours of manual work parsing PDFs and spreadsheets.
Unique Capability: Beyond simple sanctions hits, AnChain's trace and attribution tooling can identify high-risk infrastructure tied to laundering. In this case, tracing activity upstream from Chen Zhi's wallet network links funding back to CoinJoin (a Bitcoin mixer). This is a strong indicator of intentional source obfuscation and layering before funds reach the sanctioned wallet cluster.
Why This Matters: It helps investigators and compliance teams:
The Power of Automation: AnChain's activity screening identified patterns that would be difficult to spot manually:
The system automatically categorizes transactions by risk type (sanction, high-risk, unaffiliated) and aggregates volumes, making it easy to spot patterns across thousands of transactions.
Beyond Single Address Analysis: The attribution screening revealed the full network structure:
CoinJoin Mixing Service (Source)
↓
Recurring Deposit Address (1GX28y...)
↓
[Address #4] ← Primary Hub (~$1.52B received from unaffiliated)
↓
├─→ [Address #7] (sanctioned) → Unaffiliated (~$434.10M sent)
├─→ [Address #10] (sanctioned) → Unaffiliated (~$434.10M sent)
└─→ [Other Sanctioned Addresses]
This network mapping is critical for:
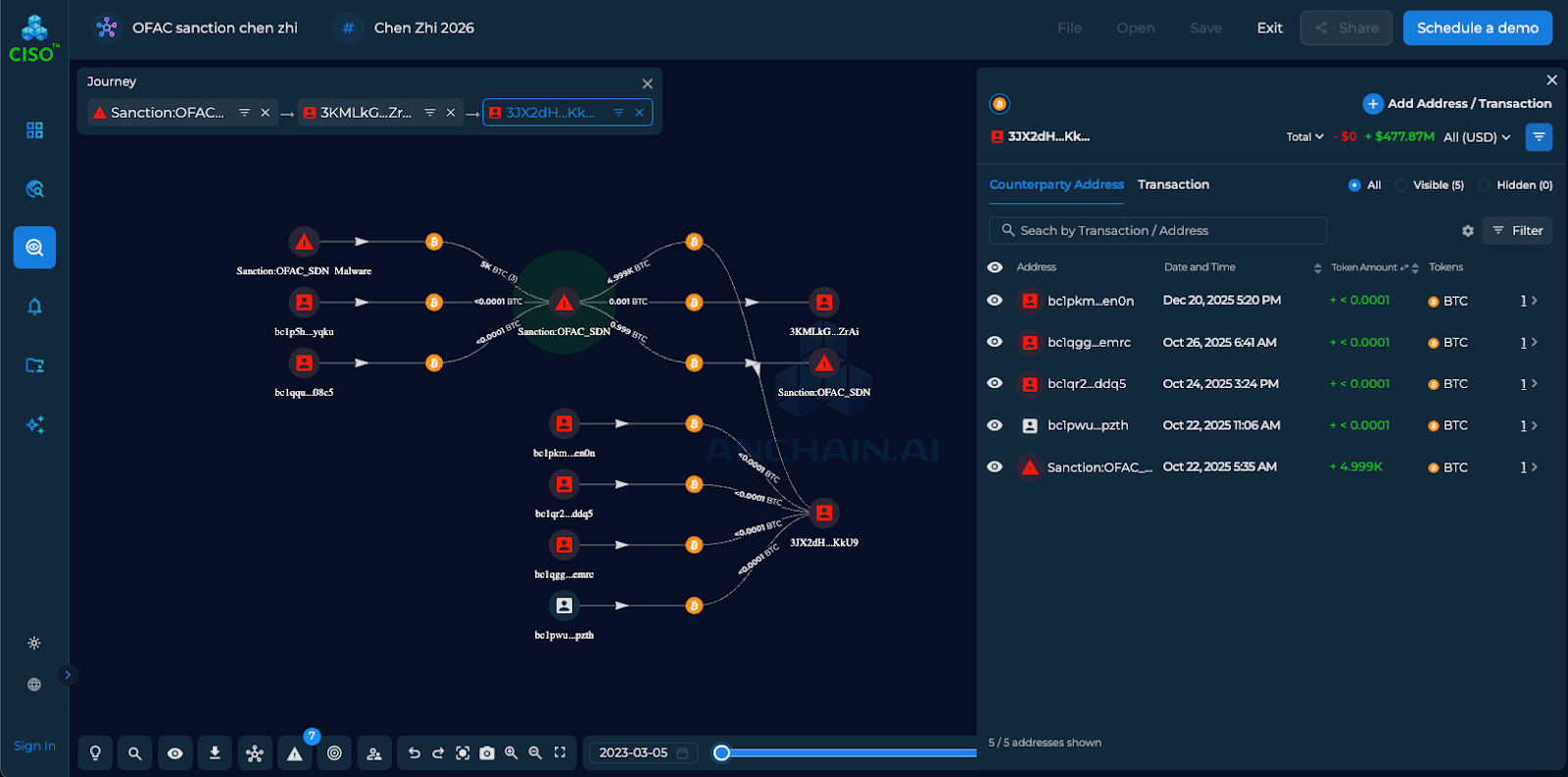
AnChain.AI platform viewable link for Prince Group sanctioned entity: https://ciso.anchainai.com/s/5qpg73lXsxU
The Chen Zhi investigation demonstrates what's possible when powerful blockchain intelligence tools are made accessible through modern protocols like MCP. What used to require:
Can now be accomplished by:
As cryptocurrency adoption continues to grow, so does the need for effective investigation tools. AnChain MCPs provide a scalable, accessible solution that makes comprehensive blockchain investigations possible for teams of all sizes.
The investigation into Chen Zhi and the Prince Group's $15 billion pig butchering operation revealed:
10 sanctioned Bitcoin addresses with confirmed OFAC listingsTransaction volumes totaling $2.5+ billion USD across the identified addressesA sophisticated money laundering network with clear operational structureConnections to high-risk infrastructure (including a CoinJoin mixing service)All of this intelligence was gathered in minutes using AnChain's MCP tools, demonstrating the power of modern blockchain intelligence platforms when integrated into investigation workflows.
For compliance teams, this means faster, more accurate sanctions screening. For investigators, it means comprehensive network mapping in minutes instead of weeks. For financial institutions, it means better risk management and regulatory compliance.
What you get:
AnChain.AI provides comprehensive blockchain intelligence and compliance solutions. Our MCP servers enable seamless integration of blockchain analytics into any investigation or AML compliance workflow.
Key Capabilities:
Learn More:
This investigation was conducted using publicly available blockchain data and official sanctions lists. All addresses and transaction hashes are documented in the full investigation report available upon request.